How to Effectively Assess the Security of Your Applications
Why Annual Penetration Testing Falls Short
Annual penetration tests, while necessary, are not sufficient for high-risk industries and Enteprise-SaaS. The rapidly evolving threat landscape means that vulnerabilities can appear at any time, leaving gaps in your security if you're only testing once a year.
By integrating security into every stage of the development process, you can identify and address vulnerabilities early. This proactive approach helps safeguard your business, protects sensitive data, and builds a foundation of trust and resilience.
What is S-SDLC?
Introducing SDLC vs S-SDLC
The Secure Software Development Lifecycle (S-SDLC) enhances the traditional Software Development Lifecycle (SDLC) by integrating security measures into every phase. This proactive approach ensures that security is a fundamental part of the development process, reducing vulnerabilities and enhancing the overall security posture of the application.
Security activities for SDLC phases
Step 1
Security Requirements
Ensure the application has foundational global security & privacy requirements that developers will use to create a secure architecture.
Define security requirements
Review functional requirements
Create security checklists
What you get
Integrating a Secure Software Development Life Cycle
(S-SDLC) into your development process is essential for creating secure, high-quality software. By embedding security practices from the outset, you can proactively identify and address vulnerabilities, streamline your workflow, and ensure compliance with industry standards.
This approach not only reduces costs associated with fixing security issues post-deployment but also enhances customer trust and satisfaction by delivering reliable, secure software.
Explore the comprehensive benefits of adopting S-SDLC and how it can continuously improve your development process to keep pace with evolving security threats.
What we do
Our Application Security Services help integrate security into different stages of the SDLC:
Our Approach
We provide tailored application security solutions that align with your specific needs and development processes.
Business-oriented
When organizations’ resources (team capacity, budgets, etc.) fall short, we prepare a solution that fits your project requirements. We will study your business context—needs, requirements, team capacity, budget constraints—and the goals you want to achieve, offering a tailored solution that aligns with your priorities and addresses your risks accordingly.
Risk-driven
A risk-driven approach is crucial for understanding which measures to take and for defining an effective security strategy. We help you identify and quantify the impact and likelihood of your risks, enabling well-informed and budget-conscious decisions with the help of threat modeling and architecture review.
Non-blocking Development
We seamlessly integrate into your SDLC by studying your process (Sprint structure, Grooming, Planning, CI/CD pipeline) and aligning our security efforts. We prioritize functionalities that require security review, ensuring security without slowing down development.
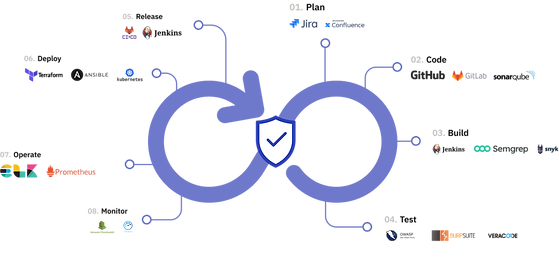
Security Automation
Embed security into every phase of the DevOps pipeline, ensuring collaboration and continuous improvement across development, operations, and security teams.
Developer DNA
Our security engineers are former developers, giving us unparalleled expertise in code review. We deeply understand software architectures and know where potential pitfalls lie in the development process. This insight allows us to identify vulnerabilities that others might overlook, ensuring your applications are robust and secure.

Seamless Integration
Let us become part of your team. We connect with you via Slack or other fast communication channels and easily integrate into any of your task management systems (Jira, ClickUp, Notion).
Methodologies
We use industry-recognized methodologies to ensure comprehensive security.
How It Works
Our approach makes navigating cybersecurity straightforward and effective. Here’s a snapshot of how we do it
Intro
-
Schedule a call with us.
-
Let us understand your business context and objectives.
-
We will prepare a proposal that addresses your needs and objectives within your available resources.
Initial Assessment
-
Evaluate existing security measures and processes (Current Profile).
-
Draft an action plan to achieve the desired objective.
-
Present the vision for your company.
Implementation
-
Introduce dedicated security experts to your team.
-
Perform regular security assessments and updates.
-
Update the SDLC workflow for more convenient collaboration, where necessary.
Support & Monitoring
-
Monitor the progress of achieving the (Objective) Target Profile.
-
Maintenance and Efficiency Check of introduced security measures.
-
Provide consultations to address any security concerns.
Our Certifications
Why Us?
Our team of experienced professionals is committed to staying current with the latest trends and technologies to provide you with the most advanced protection.
TOP5 Penetration testing Company
360° Vulnerability Detection
Developer DNA
Security Automation Experts
In-Depth Analysis
Outstanding Project Management
10+
successful security integrations
50+
clients worldwide trust us
5/5
Client Satisfaction Rate
90%
Clients return
In-depth Testing
Data Intelligence
Global Partnerships
Our Partners
Case Studies
Cybersecurity
Sekurno performed penetration testing on two apps of
a global advertising platform. The team also conducted vulnerability assessments on the client's internal and external infrastructures.
"Their expertise was evident in every aspect of the engagement"
Cybersecurity, Application Testing
Sekurno has completed a security audit and ensured compliance with ISO 27001 standards and GDPR regulations for an loT solutions company. They've consulted on all stages of the software development process.
"Our collaboration with Sekurno has consistently been seamless"
Client reviews

Max R.
As a Sekurno client, I've been impressed with their structured and effective strategies for complex security and privacy issues. Their team's expertise and responsiveness are exceptional, implementing continuous, dynamic security processes. This collaboration has addressed our immediate needs and set a clear path for ongoing security and privacy development, crucial in our evolving digital environment.
Talk to us
How lack of S-SDLC can Harm Your Business?
-
Will penetration testing disrupt my business operations?No, ethical hackers will work closely with you to ensure that testing does not impact your regular operations or service availability.
-
Why do we need penetration testing?Penetration testing helps organizations identify vulnerabilities before cybercriminals can exploit them, ensuring robust security and compliance with industry regulations.
-
What’s the difference between vulnerability scanning and penetration testing?Vulnerability scanning is an automated process to identify potential vulnerabilities, while penetration testing is a more comprehensive, manual effort to exploit and analyze those vulnerabilities.
-
What is OWASP, and why is it important?OWASP stands for the Open Web Application Security Project. It’s a nonprofit that works to improve software security. Their top 10 list of web application vulnerabilities is a crucial resource in the pentesting community.
-
What is penetration testing?Penetration testing, often called ‘pentesting’ or ‘ethical hacking,’ is a simulated cyber attack on a system, application, or network, aiming to uncover vulnerabilities that could be exploited by malicious actors.
-
How do you ensure that testing is done securely and responsibly?Our team strictly follows industry methodologies like OWASP and PTES and works in isolated environments, ensuring no data leakage or unintended disruptions.
-
Can I conduct penetration testing internally?While organizations can have internal teams perform pentesting, external teams provide an unbiased perspective and can identify vulnerabilities that internal teams might overlook.
-
What are the different types of penetration tests?There are several types, including network penetration testing, web application testing, mobile application testing, and social engineering tests.
-
What can I expect in the final report?Our detailed report provides an executive summary for management, technical findings, a threat model document, and a checklist of all tests performed.
-
How often should I conduct penetration testing?Industry best practices recommend annual penetration tests at a minimum. However, it’s ideal to test more frequently, especially if you make significant changes to your infrastructure or applications.
-
What is ‘white box’ and ‘black box’ testing?‘White box’ testing is when the tester has knowledge of the internal structures or workings of the application. ‘Black box’ testing is done without any prior knowledge of the infrastructure.
-
Is penetration testing costly?The cost of penetration testing varies based on scope, complexity, and type. However, considering the potential loss from a security breach, it’s a worthy investment for businesses.
-
What makes Sekurno different from other cybersecurity firms?Sekurno offers a comprehensive approach to cybersecurity, combining advanced pen-testing, continuous security support, and AI-assisted processes. With a dedicated team for each client and a commitment to transparency, Sekurno ensures that businesses are protected beyond mere compliance.
-
How does Sekurno ensure transparency in its services?Sekurno believes in no hidden fees and provides regular updates to clients. Every project involves at least two engineers, ensuring an unbiased approach, and we adhere to standards with checklists for all tests performed.
-
How has Sekurno benefited its clients in the past?Sekurno has a proven track record with over 80 projects completed, saving clients a cumulative $90M. We pride ourselves on a 5/5 client satisfaction rate.
-
What certifications do Sekurno's experts hold?Our team comprises experts with some of the most challenging certifications in the cybersecurity domain. This ensures that our clients receive top-notch service from knowledgeable professionals.
-
What does "security beyond compliance" mean?While many firms focus on meeting the minimum security standards set by regulations, Sekurno goes beyond that. We aim to reduce risks to the highest extent possible, ensuring that businesses are not just compliant but also genuinely secure.
-
How does Sekurno's AI-assisted process enhance cybersecurity?Our AI-assisted processes help in creating more accurate threat models, generating detailed reports, and formulating security policies. This ensures a faster response time and more efficient threat detection and mitigation.
-
How do I get started with Sekurno’s Application Security Services?To get started, you can schedule a consultation with our team. We will conduct an initial assessment of your current security posture, integrate a dedicated security expert into your team, and provide continuous support throughout the SDLC.
-
How does integrating security early (Shift-Left) benefit my business?Integrating security early, or shifting left, helps in early detection of vulnerabilities, reducing the cost and time required for remediation. It also improves the overall security posture of the application, leading to fewer security incidents and compliance issues.
-
What stages of the SDLC does Sekurno cover?Sekurno covers all stages of the SDLC, including: Requirements Analysis Architectural Design Software Development Testing Deployment Maintenance
-
What is Application Security?Application security involves integrating security practices into the software development lifecycle (SDLC) to protect applications from vulnerabilities and threats. It includes measures such as secure coding practices, threat modeling, security testing, and continuous monitoring.
-
Why is Secure SDLC important?Secure SDLC is crucial because it helps identify and mitigate security vulnerabilities early in the development process, reducing the cost and time required to fix issues. It also enhances the overall security and quality of the application, ensuring compliance with industry standards and regulations.
-
What tools and methodologies does Sekurno use?Sekurno uses industry-recognized tools and methodologies, such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), and frameworks like OWASP ASVS and NIST CSF to ensure comprehensive security coverage.
-
How does Sekurno ensure compliance with industry standards?Sekurno ensures compliance by integrating security best practices and regulatory requirements into the SDLC. We use frameworks such as ISO/IEC 27001 and NIST CSF to guide our security measures and maintain alignment with industry standards.
-
Can Sekurno integrate with our existing development tools and workflows?Yes, Sekurno can integrate with your existing development tools and workflows. We work closely with your team to ensure seamless integration of security practices into your current processes, enhancing your overall security posture without disrupting productivity.
Recent Blog Posts
An invaluable resource for staying up-to-date on the latest cybersecurity news, product updates, and industry trends.















